Why Data Security Should be Top of Mind When Buying Equipment Finance Software
In 2022, Lastpass suffered a major data breach, an event which would be consequential for any company, and was made even more so by the fact that Lastpass, by its very nature, claims to help make the digital landscape more secure. While Lastpass claimed that no customer data or passwords were compromised, some 33 million accounts were affected. Businesses around the world scrambled to ensure that their employees using the system made the necessary updates to ensure that this breach wouldn’t create a ripple effect of secondary breaches in the aftermath. Whilst they might have themselves adhered to best practices for data security and storage with zeal, one software partner’s failures could have brought down the whole ship.
Which is to say that while you might internally adhere to a high level of data security, in reality, your sensitive data is often only as secure as the software that surrounds it. We sat down with our very own Kezhen Gao, Director of IT, to learn what he looks for when evaluating new software partners for Constellation Financial Software, and we think you’ll find it instructive. These are the questions you and your team should ask when selecting the right software for your business.
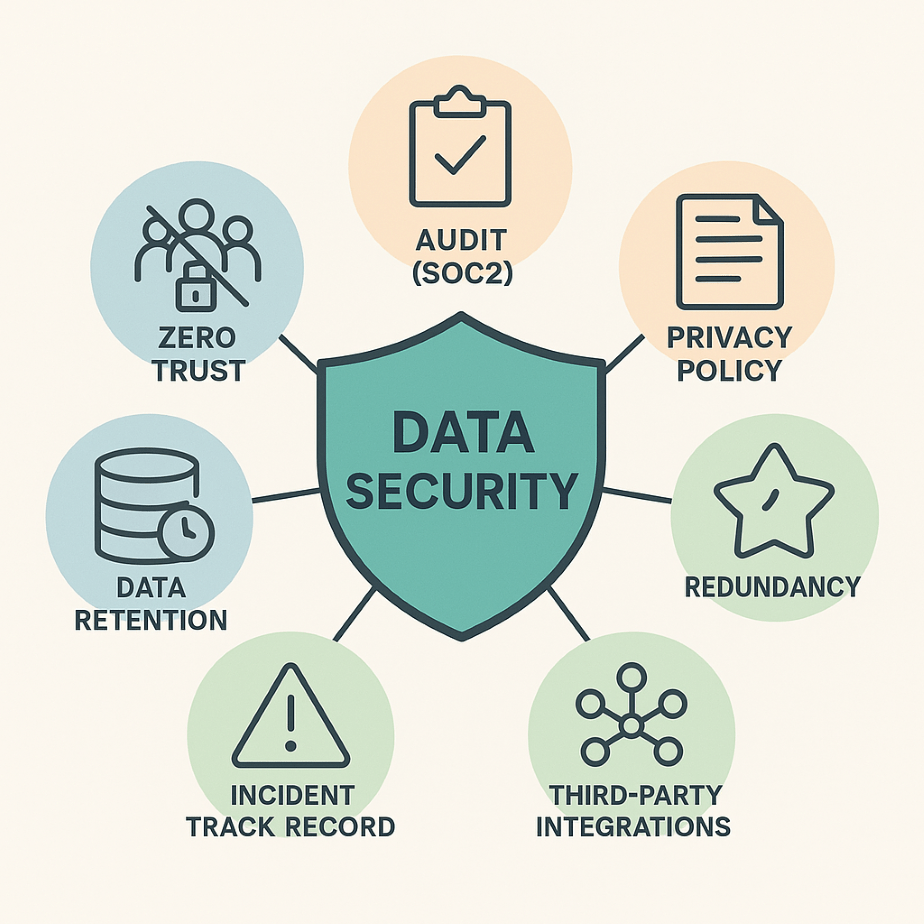
Does the software in question have a “Zero Trust” Model?
A “Zero Trust” model assumes that no user, device, or application should be trusted by default, and it means requiring strict authorization and verification for every access request. A “Zero Trust” model requires that:
- Access is verified through Multi-Factor Authentication
- Users should have “Least Privilege Access”. Users and applications should only have access to the resources they absolutely need to perform their tasks. Which is to say that employees should not have access to more than what is needed to do their job.
- All devices, whether they’re external or not, are treated with the same level of distrust.
- Systems should be micro-segmented: meaning that networks should be segmented to mitigate impact in case of a breach.
- Have they undergone any third-party audit review? For example, SOC2, HIPPA, ISO27001, PCI, etc.
We are independently audited each year under the SOC 2 Type II standard, ensuring our security practices meet rigorous industry benchmarks. Our commitment to protecting your data isn’t a checkbox exercise — it’s a core part of how we operate. With validated controls and continuous oversight, you can trust that your information is secure, compliant, and handled with the highest level of care. Choosing software that is SOC2 or similarly compliant means you can rest easy knowing the system you’re using to store data is secure.
What is their privacy policy?
At a minimum, any software provider you use should meet the legal standard as pertains to privacy for the region in which you operate. If the software is being used to process customer data, then for all intents and purposes, their privacy policy is your privacy policy, so treat it accordingly.
Understanding the nuances of a potential software partner’s privacy policy is essential.
What is their data retention policy?
When evaluating software, a solid data retention policy should offer clear, customizable retention periods, allow for both automatic and manual deletion, and distinguish between soft and hard deletes. It should support regulatory compliance (like GDPR or HIPAA), include backup and archiving rules, and allow for legal holds when needed. The policy should also ensure data can be exported before deletion and that third-party integrations respect the same rules.
Are they reputable and stable?
While startups undoubtedly come with considerable buzz, they also come with risk. A stable company is likely providing software that’s less likely to come with major bugs and vulnerabilities leaving you and your clients at risk.
When choosing a software partner, reputation and stability are crucial because they’re strong indicators of reliability, accountability, and long-term support. A reputable provider has a proven track record of delivering quality solutions and standing behind their work — which reduces your risk and increases your confidence in the relationship.
Stability matters because onboarding is rarely a one-and-done effort; it often involves ongoing collaboration, updates, and support. You want a partner who will be around for the long haul — not one that might disappear, pivot directions, or go out of business, leaving your systems vulnerable or unsupported.
In short: a reputable, stable partner helps protect your investment, ensures continuity, and builds trust in the software ecosystem you’re creating.
Do they have a redundancy plan and a disaster recovery plan?
When evaluating software, it’s critical to confirm the company has a robust redundancy and disaster recovery plan. In the event of a system failure, data loss, or breach, a strong recovery plan ensures operations can be quickly restored with minimal disruption.
Look for clear strategies around data backups, failover systems, and incident communication protocols. A reliable provider should have multiple layers of data protection across geographically distributed servers, ensuring your data remains secure even if one site is impacted.
Redundancy isn’t just about preventing data loss — it’s about maintaining operational continuity and protecting your business from costly downtime.
What is their track record with past security incidents?
A company’s history can provide valuable insight into how seriously they take security. Take the time to investigate any past security incidents and evaluate how the company handled them. Did they respond promptly and transparently? How long did it take for them to resolve the issue, and what steps have they taken since to strengthen their security protocols? Understanding how your software partner has addressed breaches, if any, will give you confidence in their ability to manage potential future incidents. Transparency and accountability are key indicators of a provider who is serious about protecting your data.
Are they transparent about their security practices and updates?
Security is not a one-time effort—it’s a continuous process. Your software partner should be transparent about their ongoing efforts to strengthen their security posture. Regular updates and patching are essential to keeping vulnerabilities at bay. This transparency should extend to sharing information about what security features are being developed, how updates are being rolled out, and how they communicate any changes or vulnerabilities that may affect you. Ideally, your partner should provide detailed security documentation that allows you to assess their practices and stay informed about how they’re evolving their security measures.
How do they handle third-party integrations?
In today’s interconnected world, most software solutions rely on integrations with other systems. While these integrations can enhance functionality, they can also open the door to security vulnerabilities. It’s crucial to evaluate how a potential software partner manages third-party integrations. Do they vet third-party providers to ensure that their security practices align with your own standards? Are their APIs secure, and do they adhere to strict access controls? A partner who understands the risks posed by third-party connections will take the necessary steps to mitigate them, ensuring that your entire tech stack remains secure.
Final Thoughts
Choosing a software partner is a critical decision that can have far-reaching implications for your company’s security posture. By evaluating potential partners through the lens of these essential criteria, you can ensure that the tools you rely on are not only efficient and functional but also secure and resilient in the face of evolving threats. In an age where data breaches have become all too common, your company’s security is only as strong as the software that supports it. Making thoughtful, informed decisions about your software partners is the first step in ensuring that your digital landscape remains safe and secure.
At Constellation Financial Software, we understand the importance of robust security and privacy practices. This is why we’re SOC2 Type 2 compliant. By working with trusted partners who meet these rigorous criteria, we help ensure that our clients’ data remains protected—no matter the challenges the digital world may throw our way. If you’d like to learn more about our approach to security or discuss your own software needs, don’t hesitate to reach out. We’re here to help guide you through the complexities of today’s digital security landscape.


